KeyAuthority
KMIP (Key Management Interoperability Protocol) 金鑰管理 |
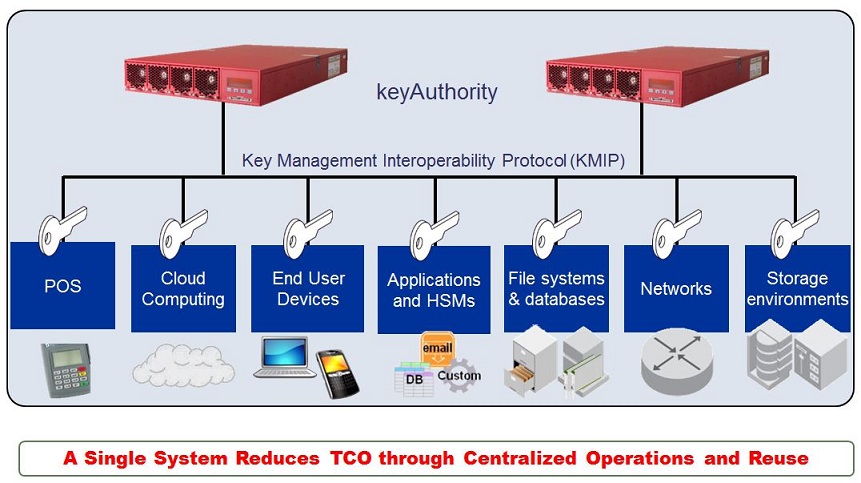
Proven solution for centralizing key management
keyAuthorityR version 4.0 from Thales e-Security is a hardened cryptographic key manager that provides high levels of assurance to users of applications and systems with embedded encryption. keyAuthority supports widely-accepted industry standards, including the Key Management Interoperability Protocol (KMIP) standard, to allow comprehensive endpoint interoperability. Centralized administration provides consistent key lifecycle policy enforcement with reliable auditing to ensure data recovery and long-term business continuity. Enterprises now have a high performance key management solution that scales to support encryption requirements today and in the future. Its security boundary, which includes the entire chassis for higher assurance protection, has been validated to FIPS 140-2 Level 3.
Benefits of keyAuthority
- Automates key lifecycle management across global enterprises.
- Lowers risk of breaches with high-assurance, reliable hardware.
- Accelerates encryption deployment through pre-qualified solutions.
- Centralizes policy by using a single system to access and audit.
- Reduces management overhead by integrating encryption silos.
Security Features
- Attack-resistant and tamper-evident hardware delivers high assurance protection for keys and the information it safeguards.
- Automated key lifecycle policies make it easier for organizations to implement best practices in key management and enforce consistent security.
- Multi-factor authentication, role-based access controls, and support for dual controls enable strong separation of duties and ensure authorized access to keys and devices.
- Secure audit facilities enable reliable compliance reporting and verification of controls in place.
Operational Features
- Centralized administration streamlines management of keys and encryption processes across even the most complex, heterogeneous global environments, enabling organizations to implement a consistent security model and reduce operating costs.
- A performance-optimized solution that includes key backup and synchronized key replication helps to ensure high availability.
- Pre-qualification of leading encryption products simplifies and accelerates deployment for both proprietary and KMIP-based solutions.
- Flexible, unified interface extends to a broad range of existing and emerging encryption products, so you can scale new enterprise applications with confidence.
- Redundant field-serviceable fans, dual hot-swap power supplies, and other redundant hardware features ensure a fault-tolerant solution suitable for high-availability applications.
- Group and domain separation supports multi-tenancy applications, enabling service providers to streamline operations.
產品規格
Cryptographic algorithms supported
-
Symmetric:AES (128, 192, 256),
TDES (3 KEY)
- Asymmetric:
RSA (2048, 3072, 4096, 5120, 6144, 8192)
- Other:
Elliptic Curve,
Opaque Object,
Secret Data
- Generate symmetric and asymmetric; other types, storage only.
Certifications
- FIPS 140-2 Level 3 (certificate #1777 for v3.03 firmware)
- UL, CE, FCC, C-Tick
- RoHS
Applications supported
Below is a non-exhaustive list of applications that utilize proprietary protocols or KMIP for key management interoperability and have been tested by Thales.
- Brocade Encryption Switch and FS8-18 Encryption Blades for DCX Chassis
- IBM encryption-ready tape (TS-Series) and disk (DS-Series) storage line products
- Hitachi Virtual Storage Platform (VSP), and Hitachi Unified Storage (HUS) VM and 150
- Quantum Scalar tape libraries
- Sepaton S2100-ES3 series 2925 Backup and Recovery Appliance
KMIP Client SDKs supported from Thales ASAP partners:
- Cryptsoft Key Management Client SDK
- Project 6 Research SKC Secure KMIP Client SDK
參考資料:
KMIP (http://en.wikipedia.org/wiki/Key_Management_Interoperability_Protocol)
FIPS 認證 (http://csrc.nist.gov/groups/STM/cmvp/documents/140-1/140sp/140sp1777.pdf)
請與我們連絡: (02)77294248
玉山科技 版權所有 © Copyright AsiaPeak 2006, All Rights Reserved
|

